by Ken Macon, Reclaim The Net:
 Notifications are increasingly being shown to be a privacy risk.
Notifications are increasingly being shown to be a privacy risk.
Many iPhone applications have been found to be exploiting iOS’s push notifications to secretly harvest user data, a practice that potentially aids in building tracking profiles. This revelation was made by mobile researcher Mysk, who also added that these apps could bypass Apple’s stringent restrictions on background app activities, thereby posing a privacy threat to its users.
TRUTH LIVES on at https://sgtreport.tv/
Get our guide on protecting yourself from notification surveillance here.
While Apple’s App Store review guidelines explicitly prevent such data collection practices, apps have been found to engage in this activity rather surreptitiously. According to Mysk, many well-known apps with large user bases clandestinely send user details back to their servers upon receiving or acknowledging push notifications, raising concerns about privacy.
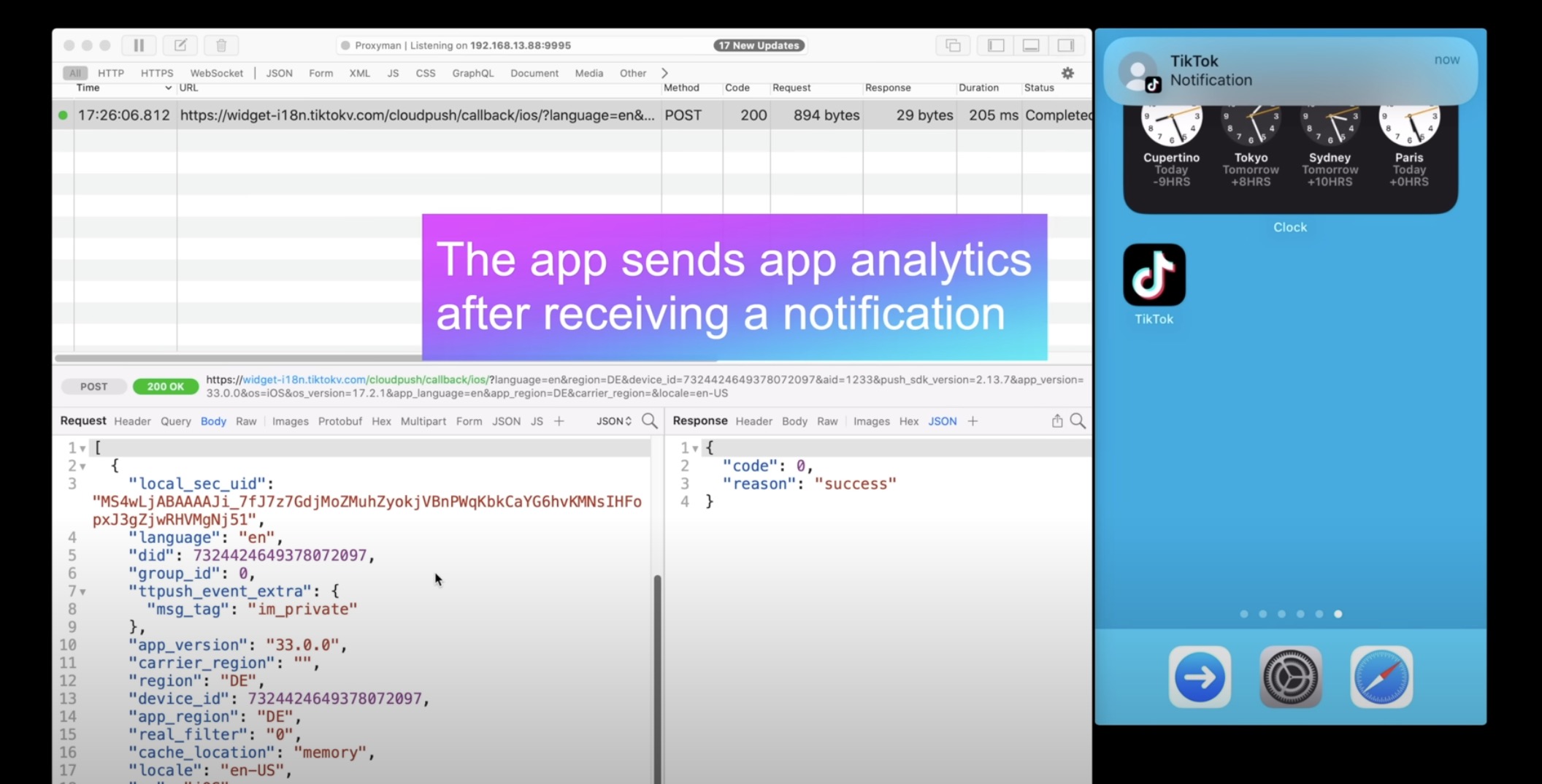
Apple’s iOS operating system is designed to minimize security risks and resource consumption by preventing apps from running in the background. Essentially, an app’s execution is suspended and eventually terminated when not in use. However, a system introduced in iOS 10 enabled apps to launch silently in the background to process incoming notifications before they were displayed on the device. Once this action gets completed, the app is again terminated.
Mysk’s research unearthed extensive abuse of this feature, with apps using this as an opportunity to send data back to their servers. The transmitted information may vary depending on the app, but it typically included data like system uptime, language settings, available storage, battery status, device model, and screen brightness.
This collected data can potentially be leveraged to create tracking profiles.
In December, it was uncovered that several governments were seeking access to push notification records from Apple’s and Google’s servers for espionage on users.





 Russian Nuclear Doctrine TRIGGEREDBREAKING:
Russian Nuclear Doctrine TRIGGEREDBREAKING: 