from The Conservative Treehouse:

Independent journalist Matt Taibbi has released the sixth installment after review of more Twitter File data [SEE HERE]. Keep in mind, the research group containing Mr. Taibbi are only seeing the consequences side of the content removal process. What specifically happened in/around the portal of information flowing into Twitter HQ is a different division. Taibbi et al are only seeing the consequences from the requests that entered the Twitter system.
TRUTH LIVES on at https://sgtreport.tv/
[Twitter Release #6, Here]
The first section of Taibbi’s analysis is the most interesting. Having tracked the issue for several years, I would modify some of the descriptive language Taibbi presents yet agree with the overall context of his presentation.
Taibbi begins by noting, “Twitter’s contact with the FBI was constant and pervasive, as if it were a subsidiary.” I would safely take that a step further, yes there is a subsidiary relationship; however, as years of government involvement continued by 2016 Twitter became the subsidiary of DHS, not vice-versa. This dynamic within the relationship explains some of the more curious elements that Taibbi struggles to fully understand.
Notice the timing of escalation by DHS/FBI: “The FBI’s social media-focused task force, known as FTIF, created in the wake of the 2016 election, swelled to 80 agents and corresponded with Twitter to identify alleged foreign influence and election tampering of all kinds.”
As we have noted from the lead into and out of the 2016 election, the surveillance state took action specifically to protect itself from President Trump. This activity included the NSA, FISA court, FBI, DOJ-NSD, CIA, ODNI while specifically and purposefully enmeshing the Senate Select Committee on Intelligence (SSCI).
Protecting Washington DC from the risk President Trump represented was a whole of government approach. The executive and legislative branches worked together and weaponized national security claims to involve the judicial branches in the effort. In the aftermath of the 2016 election outcome, now we see social media being pulled further into the approach.
 The next three paragraphs are key in this Taibbi outline:
The next three paragraphs are key in this Taibbi outline:
8. Federal intelligence and law enforcement reach into Twitter included the Department of Homeland Security, which partnered with security contractors and think tanks to pressure Twitter to moderate content.
Highlight: “security contractors,” now where have we heard that before? Yes, the same FBI contractor access to raw/bulk NSA metadata that was discovered being extracted in the height of the 2016 GOP nomination contest. In the aftermath of the election, and in coordination with the Twitter context, now those same security contractors are part of the surveillance system generating actionable items.
9. It’s no secret the government analyzes bulk data for all sorts of purposes, everything from tracking terror suspects to making economic forecasts.
Here’s where Taibbi comes dangerously close to realizing the inflection point created by President Obama and AG Eric Holder. Prior to the arrival of the Obama administration the bulk data was a process of collection by the NSA (while looking outward for threats and limited in review by 4th amendment protections) and then delivery to the Office of the Director of National Intelligence for transfer to DHS and FBI in order to take action on anything flagged.
When the flagged data was transferred into and out of the ODNI, the constitutional and lawful processes around the 4th amendment needed to be applied. That’s where the FISA court comes into play and applications for surveillance, that pass through the DOJ National Security Division (DOJ-NSD), based on the intelligence data from the ODNI office, are put together.
The NSA was/is monitoring the raw data with a radar turned outward toward foreign entities. When something is flagged, that data is then transferred to the ODNI and exits toward the Dept of Homeland Security. The fourth amendment protection against unlawful search and seizure of private papers is supposed to apply when the data leaves ODNI. Before the FBI can use anything, the DOJ-NSD has to get a warrant, either from a federal judge or the FISA Court depending on the issue.
This process was what Barack Obama and Eric Holder worked around as they created a quasi-constitutional surveillance system. That’s where Taibbi’s next paragraph comes into play. Remember, even though President Trump was in office, the system operators in the institutions were from the Obama-Holder era:
10. The #TwitterFiles show something new: agencies like the FBI and DHS regularly sending social media content to Twitter through multiple entry points, pre-flagged for moderation.
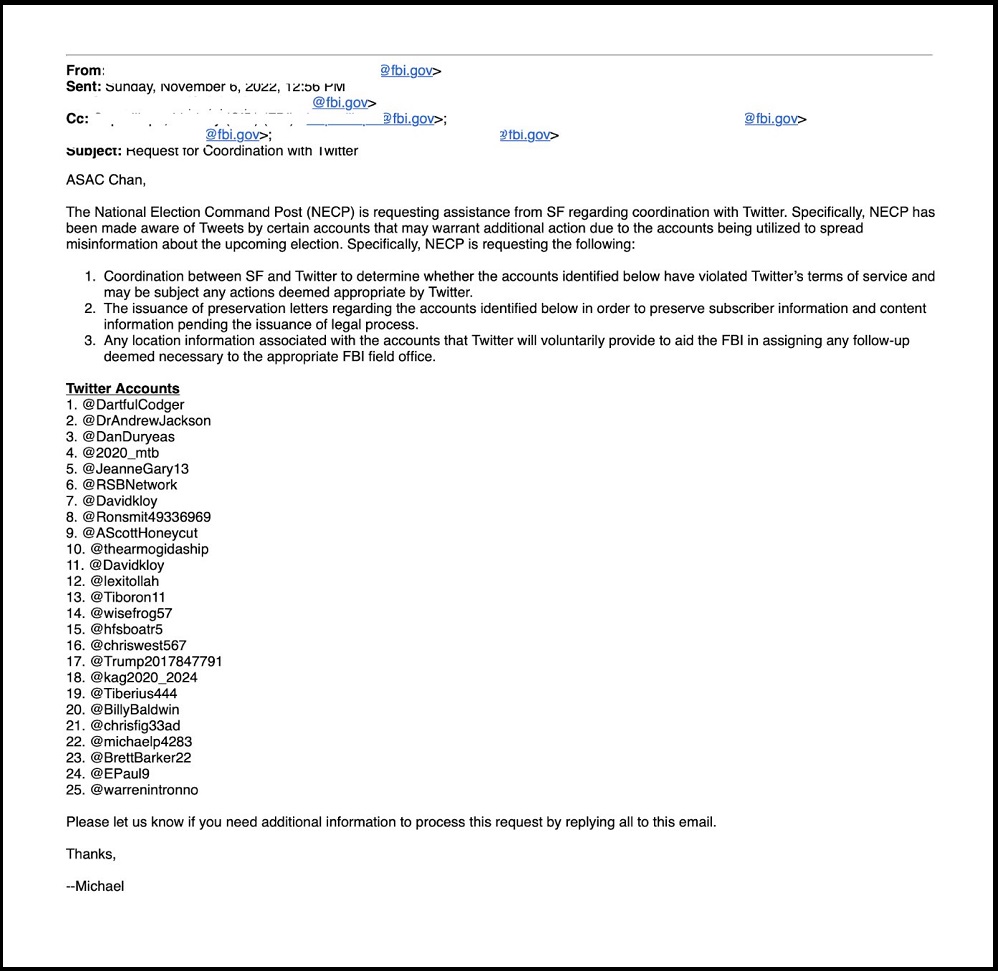
Security contractors were reviewing the public information pages, then transmitting results to DHS and FBI…. who would then use their portal connection into Twitter to make “pre-flagged” requests. What type of requests? Example:
This example is only on the subject of the 2020 election; however, you can see what bullet point #3 requests, “any location information associated with the accounts that Twitter would voluntarily provide.”
Don’t get too hung up on the example, because it only references a priority of looking at the 2020 election. Instead ask yourself the bigger question, what other priorities would be in the mind of political ideologues within DHS and FBI? What other DHS tasks, DHS assignments and FBI operations would take place that would benefit from the networking between the government and social media?
In 2011 the DOJ was using IRS filings to conduct investigations of Americans. That was what the entire IRS Tea Party scandal was really about. It wasn’t the IRS wrongdoing that led to the class action settlement, it was the DOJ origination of a request for information from the IRS about the 501-c (3)(4) groups, specifically their “schedule B’ forms, that triggered the problem starting.
After the IRS issue surfaced publicly in 2012 the DOJ immediately dropped their use of the data that was contained on 21 CD-ROMS delivered by the IRS.
Aided by advances in technology, the Obama administration switched to surveillance via direct review of available metadata. Social media platforms were enlisted as DHS partners under the auspices of ‘national security’, and suddenly there was a full-fledged surveillance state underway.
Read More @ TheConservativeTreehouse.com